The Structure Behind the GSMA-conforming eSIM for Consumers
In March 2018, the GSMA released the eSIM Whitepaper, which outlined how remote provisioning for consumer eSIMs worked and how it was structured.

In March 2018, the GSMA released the eSIM Whitepaper, which outlined how remote provisioning for consumer eSIMs worked and how it was structured; now we would like to explain the concept as simply as possible.
The Consumer Solution is a Pull Model
While the IoT and M2M (machine to machine) solutions are known as server-driven push models (where the server is the source), the consumer solution begins with the user or device and is known as a client-driven pull model. So, with M2M solutions, the endpoint device is usually in a passive state and the server side will initiate commands. But with consumer solutions, the user that wants to use the eSIM will operate the endpoint somehow, causing the provisioning sequence to start there – in turn, the server will return an appropriate response in answer to the actions taken by the client (user). What we are calling the server here is actually the Subscription Manager, commonly referred to as an SM, which we will further explain later.
The Setup of Remote SIM Provisioning
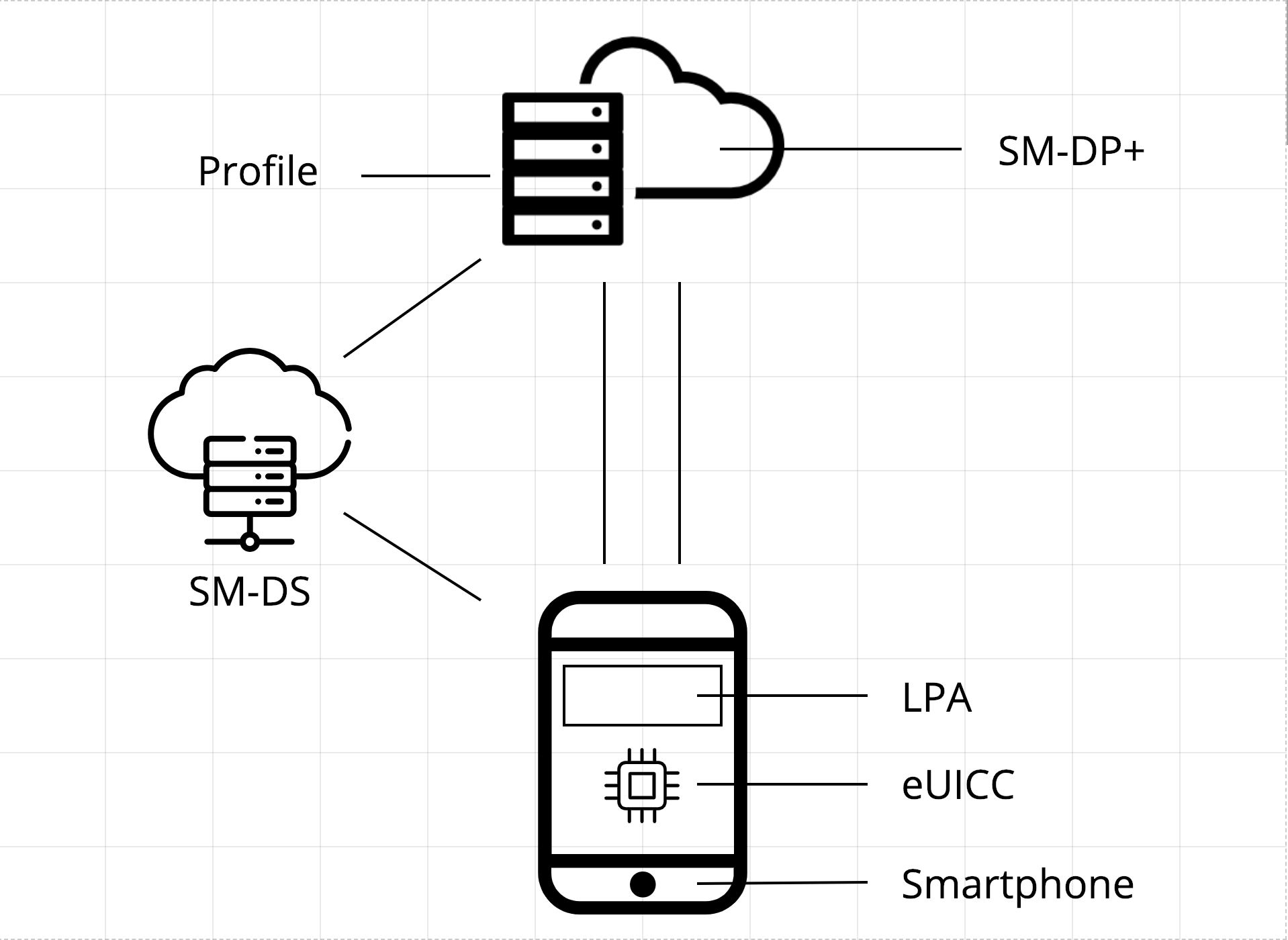
Generally, a server known as a Subscription Manager – Data Preparation + (SM-DP+), a server known as a Subscription Manager – Discovery Server (SM-DS), and a set of functions known as a Local Profile Assistant (LPA) form the basic setup for an eUICC.
First, an eUICC is an element that is equivalent to the chip in a physical SIM card, which is built into a smartphone and can hold multiple profiles.
A profile is something that contains information or contract information from your service provider (carrier), such as the number assigned to your eSIM. For a physical SIM card, this is written into the SIM itself, while an eSIM can download this information from the network using OTA (over-the-air) technology. (The sequential flow that arises with the download of this profile is called provisioning.)
What’s known as the SM-DP+ is responsible for maintaining and managing these profiles, and it will carry out processes such as the enabling, disabling, and deletion of profiles. It also ensures a secure connection when a profile is sent to the eUICC.
The LPA is a set of functions that downloads encrypted profiles to the eUICC. It further acts as the local (device) user interface for the management of the downloaded profiles. The core functions of the LPA can also be built into the eUICC as an application.
The SM-DS functions as a go-between, allowing the SM-DP+ to locate the eUICC (device) without needing to ascertain what network the eUICC is connected to. Simply put, it acts as a secure notice board where the SM-DP+ can send a notification. The SM-DP+ then tells the LPA that it sent a notification and that a profile can be downloaded, and the internal LPA will then go receive that notification and commence the download of the profile.
Safety Aspects and the GSMA Verification Program
Because the eSIM is an incredibly vital element that controls communication and there are many cases where the information it contains about the contracting party can be used for various authorizations, its security is considered to be as important as that of credit cards, if not more important. Due to this, the GSMA has arranged a verification program for eSIM manufacturers and SM-DP+/SM-DS providers, establishing stringent security and functionality criteria. Providers that obtain the GSMA’s verification/approval are then able to take part in the GSMA-approved Consumer Solution Ecosystem. If one wants to provide remote provisioning for iPhones, for example, they will have to comply with the criteria outlined by the GSMA and then receive approval. This is the structure with which the safety of eSIMs, to be used by hundreds or thousands of millions of people from now on, is guaranteed.

